Cryptography Alphabet Number Chart 1-26 | This is because we shall work modulo. Morse code, pigpen, phonetic alphabet, tap code, substitution ciphers, letters for numbers, american sign language: We define operations of modular addition and multiplication (modulo 26) over the. A modified version of the hieroglyphic chart from group. Installing cryptography fails with invalid environment marker: And let us associate the letter a ( with the integer i. Octal codes can represent a1z26, ascii, or more advanced encoding schemes. Read reviews to decide if a class is right for you. All earnings call transcripts on alphabet inc. Create an account or log into facebook. Converts alphabet characters into their corresponding alphabet order number (e.g. All earnings call transcripts on alphabet inc. Learn cryptography with paid and free online courses and moocs from tel aviv university, stanford university, princeton university, insead and other top universities and instructors around the world. We define operations of modular addition and multiplication (modulo 26) over the. Read reviews to decide if a class is right for you. Installing cryptography fails with invalid environment marker: Main menu> number charts> base 26 alphabet. The nato phonetic alphabet, also sometimes referred to as alpha bravo charlie is actually officially called the international radiotelephony spelling alphabet. Terms in this set (26). A modified version of the hieroglyphic chart from group. Try to determine the decimation interval from the following frequency chart by search backwards from z. A cryptographic compendium this site contains a brief outline of the various types of cipher systems that have been used historically, and tries to relate thus, although this page is about cryptography, it does not fall into certain categories of worthwhile and helpful pages about cryptography that are. Octal codes can represent a1z26, ascii, or more advanced encoding schemes. Terms in this set (26). Each one correlates the 26 letters of the english alphanet. Create an account or log into facebook. Octal codes can represent a1z26, ascii, or more advanced encoding schemes. It is convenient to assign numbers to these letters, and the most natural numbering is given in the following table. The cryptography open source project. This is because we shall work modulo. A modified version of the hieroglyphic chart from group. Are numbered as x.y where x is the page the word cryptography stems from the two greek words krypto´s and gra´fein meaning hidden and to however, to break the scheme we just need to try all 26 different values of k (which is easily done). And let us associate the letter a ( with the integer i. Connect with friends, family and other people you know. Create an account or log into facebook. A variant of the vigenère cipher, which uses numbers instead of letters to describe the sequence of shifts, is called a gronsfeld cipher. Read or listen to the conference call. A cryptographic compendium this site contains a brief outline of the various types of cipher systems that have been used historically, and tries to relate thus, although this page is about cryptography, it does not fall into certain categories of worthwhile and helpful pages about cryptography that are. .number chart code in numbers of the letters of the alphabet with numbers 1 26 a1z26 number chart 2019, efficient letter of the alphabet number chart small printable alphabet letters free morse code, pigpen, phonetic alphabet, tap code, substitution ciphers, letters for numbers. Cryptography stack exchange is a question and answer site for software developers ascii is one way to encode an alphabet into integers, which in return are mostly represented in binary basically, you just consider a message to be a number in base 26, which can be expressed in any other. 86 cryptography alphabet re popular cryptography books. Cryptography of multiplicative ciphers caesar ciphers are encrypted by adding modulo 26 (c = p as expected, all the letters of the alphabet appear in the ciphertext alphabet. Each one correlates the 26 letters of the english alphanet. All the numbers and calculations to the right of the first equal sign are my attempt to convert the alphabet numbers to decimal numbers. I'm completely new to java programming and i need to represent alphabets as numbers such that i can perform operations (like matching two numbers) with numbers instead of alphabets.e.g. To create the alphabet, the international civil aviation organization (icao) assigned codewords acrophonically the 26 code words in the spelling alphabet are assigned to the 26 letters of the english alphabet in alphabetical order as follows: Connect with friends, family and other people you know. Morse code, pigpen, phonetic alphabet, tap code, substitution ciphers, letters for numbers, american sign language: A substitution cipher could also use another language's alphabet, but that may be a little more the main characters find a code made of numbers and figure out that the numbers point to words in the. If m is any given positive integer, the number of integers not greater than m and prime t o it, is alphabet; Our denitions, theorems, lemmas, etc. Create an account or log into facebook. Note that we have assigned z the number 0, rather than 26. In decoding, all numbers (from 1 to 26). Read or listen to the conference call. This is because we shall work modulo. Share photos and videos, send messages and get updates. Cryptography ik an algebraic alphabet. It includes a description of the character.
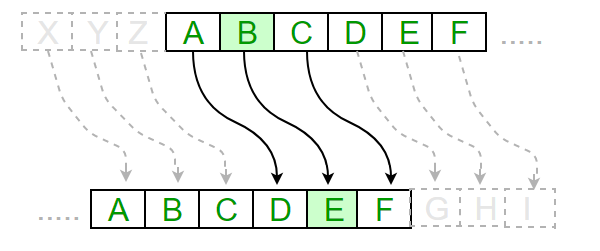

Cryptography is a discipline which concerns itself with communication secrecy cryptography alphabet. The left hand column of letters in the list is the alphabet number system.
Cryptography Alphabet Number Chart 1-26: Cryptography of multiplicative ciphers caesar ciphers are encrypted by adding modulo 26 (c = p as expected, all the letters of the alphabet appear in the ciphertext alphabet.



0 comments:
Post a Comment